Skip to the content.
Quiz 1
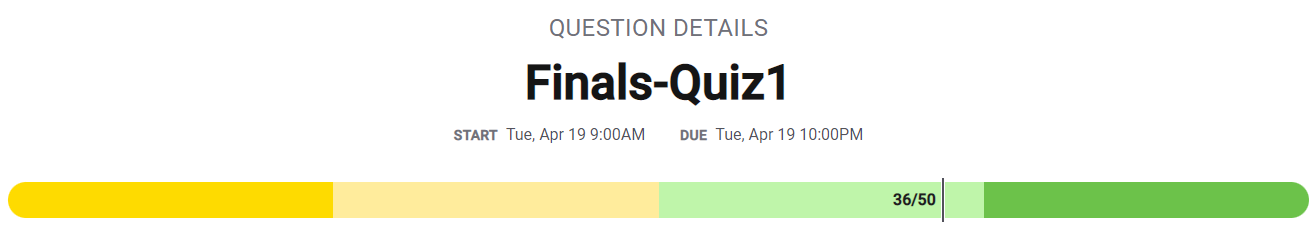
Score
Quiz Corrections
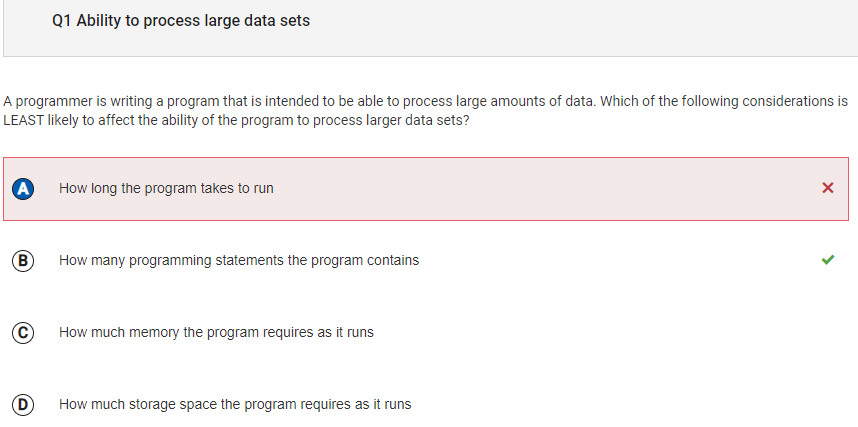
- I got question 1 wrong because when you process data, the time it takes and the ability to process it is affected.
However, B is correct because the number of statements does not affect how long it will take, and it will not be affected as much.
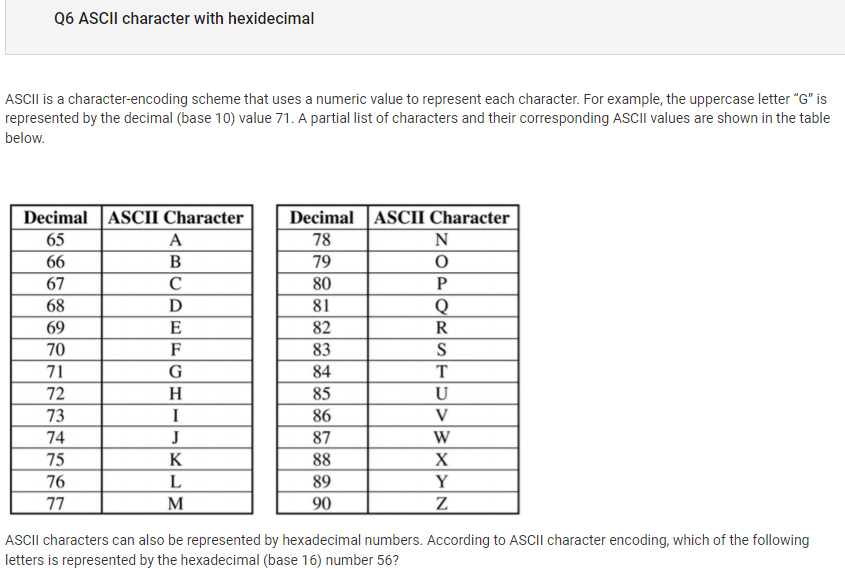
- I got question 6 wrong. It should be V, which is 86, since base 16 with hexadecimal number 56, that would be 5 times 16, getting 80. 80 + 6 is 86, so V is correct.
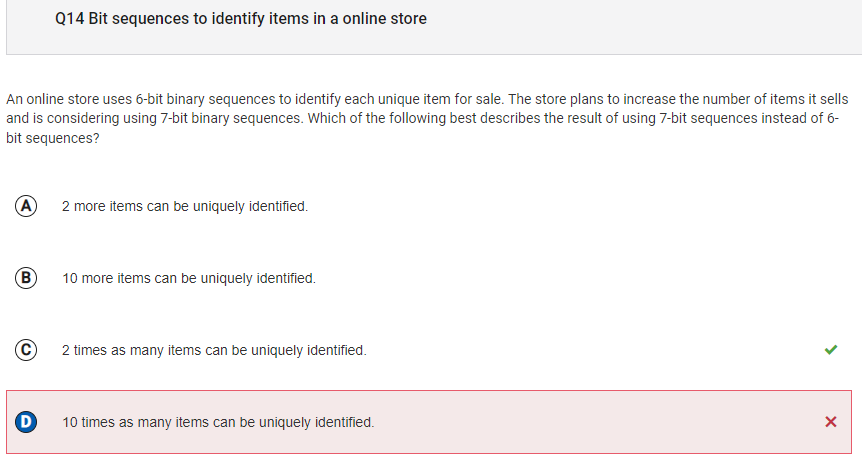
- I got question 14 wrong. This is a got to know, which I did not know. 2 times as many items should be identified because using 7-bit binary sequence can be 128,
which is 2 times as much as 6-bit binary sequences.
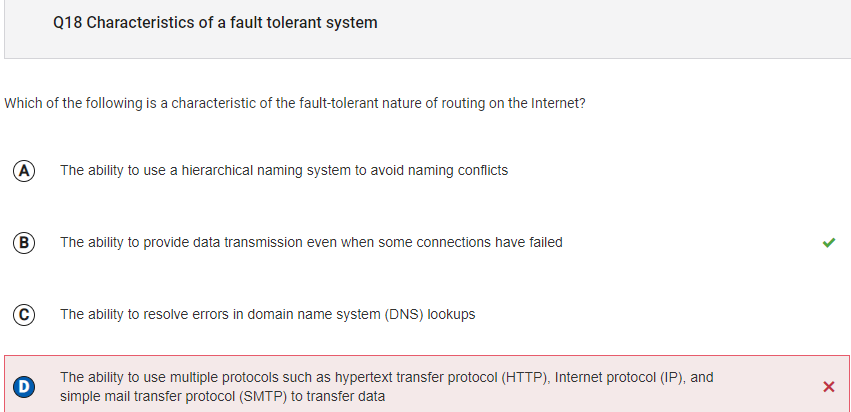
- Fault tolerance allows for things to work even if one connection fails. Using multiple protocols does not affect fault tolerance. Data can still be transmitted
if some connections fail, since the internet is fault tolerant.
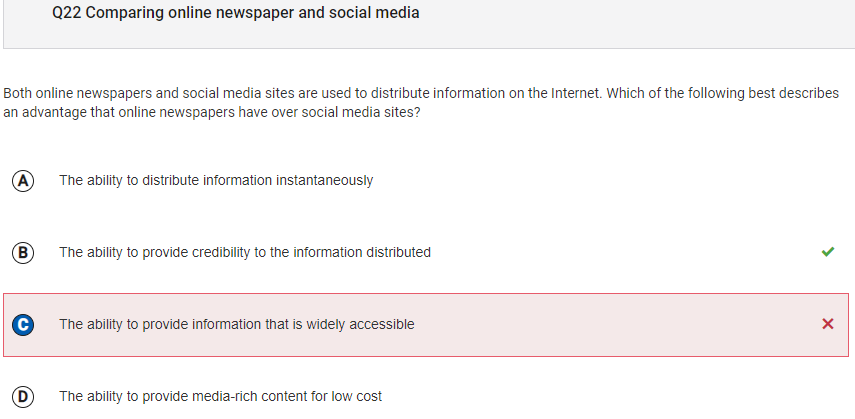
- I got question 22 wrong. Social media is free and as well as newspapers, they can have information and news displayed to the public. Open and accessible.
Newspapers can give credibiltiiy, unlike social media, because there needs to be credit given when the topic os on a newspaper, which everyone can see, unlike
social media, which not evveryone might care about.
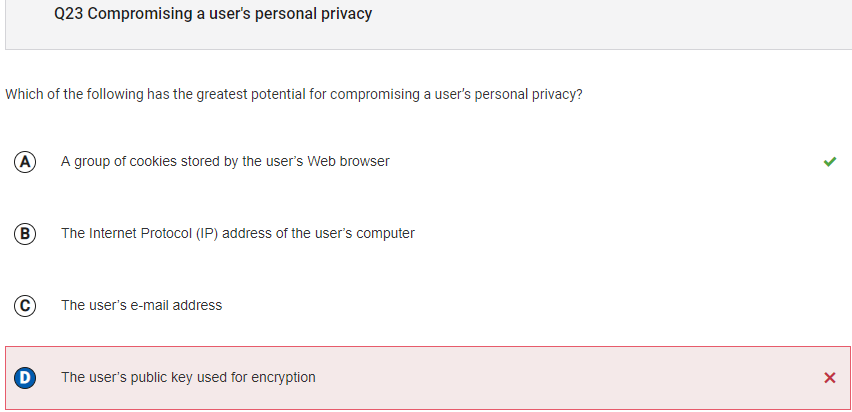
- A public key encryption can not compromise a user’s privacy, since the public key will not have any personal information. However, cookies can allows for websites
to collect information about the user.
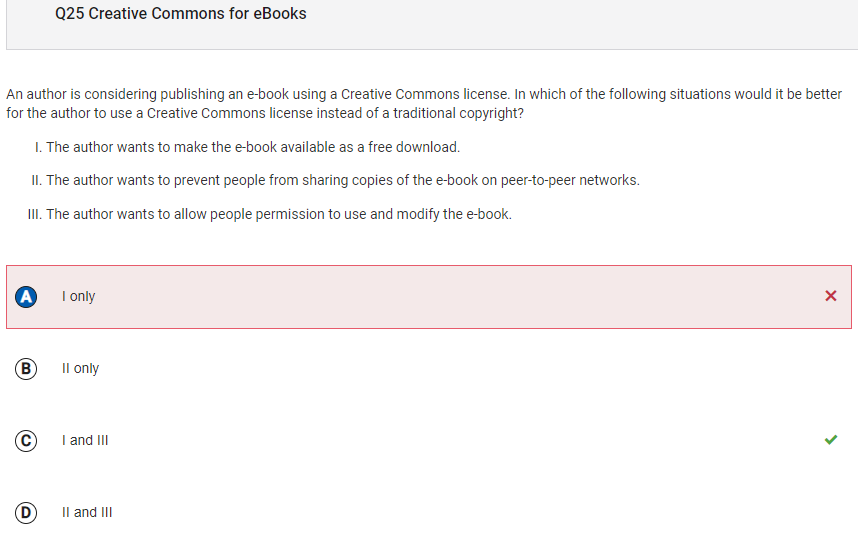
- I got question 25 wrong. It should also be #3 because it is a got to know. A creative commons license can allow the author to make restrictions on what the
users can modify.
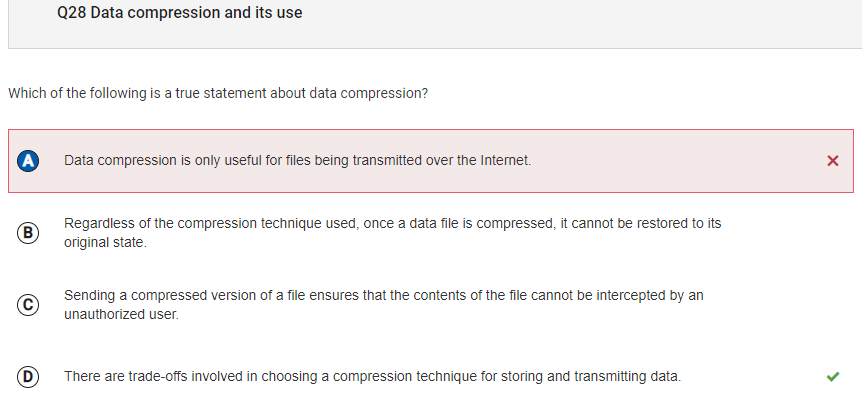
- I got this question wrong. There is lossless and lossy compression. In lossy compression, the data can be packaged, sent, and then put back together, but some
data could be lost. This shows how there are trade offs, as the task can get done, but some data can be lost.
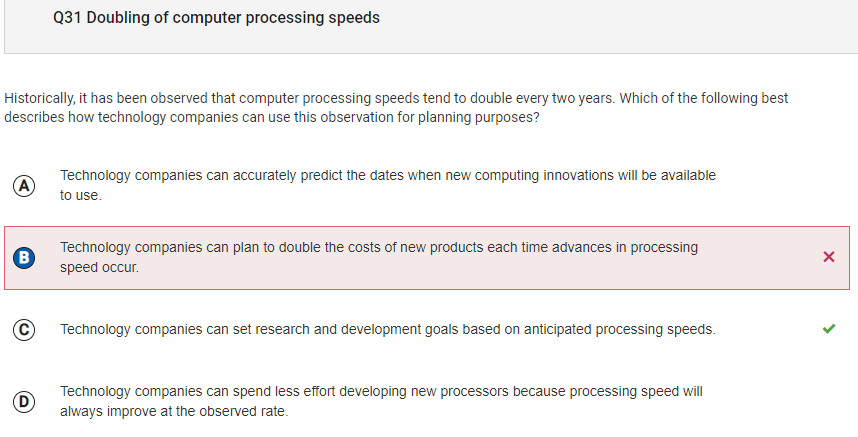
- I got this question wrong because the answer I chose is not completely true. Companies don’t have to double the cost if processing speeds get better.
If they can figure out when processing speeds get better, this can allow for plans on what to do for the improvement.
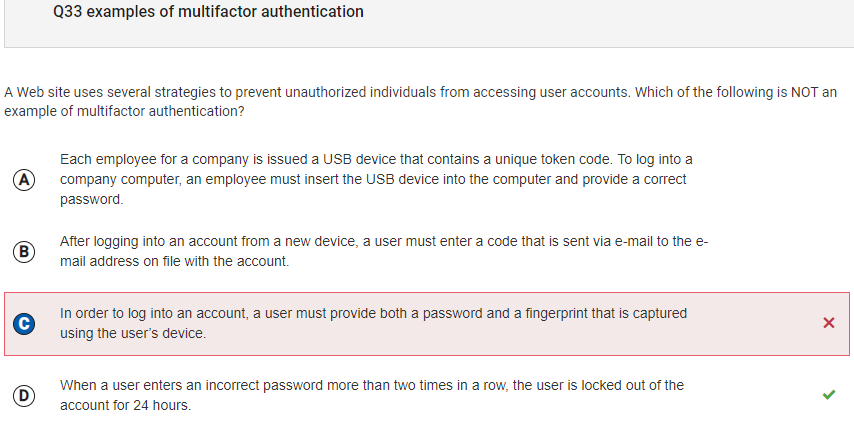
- I read the question wrong. I thought I was supposed to choose the one that was an example of multifactor authentication. The correct answer is D because
it is not multifactor authentication. It does not have multiple parts to the login of an account. It is privacy, but not multifactor.
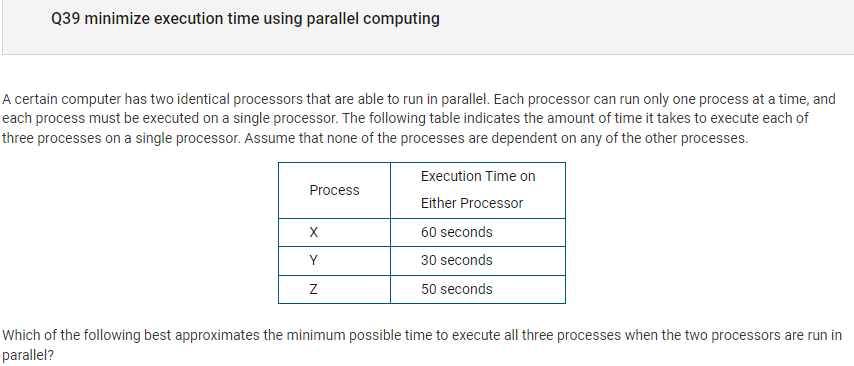
- I got this question wrong. When you run a process and one finishes before the other, the other one can have the other process, If x and y are run at the same time, y wil finish before x, so that procesor will process z. y and z combined will be 80 seconds, which is the minimum time.
- Routing is not specified, it can be dynamic. Protocols are agreed-upon sets of rules that specify the behavior of a system. Protocols used on the Internet enable devices from different manufacturers to communicate in a standard way.
- Storing information can make the user’s information not private. This means the information can be negatively affected. However, pages will still be accessible
if it hasn’t been used in a while. ISP only affects how requently pages will be opened.
- Copying pixels loses the RGB values of the pixels. If you reverse the colors, you can reverse it again to get the orginal, so it is lossless compression.














